Introduction
Passwords are words, strings of characters, or some form of interactive message used to prove identity and gain access to a resource or a place. They constitute the first line of defence for computer-based technologies and were used for millennia as the Roman military were reportedly using passwords to distinguish allies from enemies [1]. Today, even if attack-resistant validation schemes exist, passwords constitute the most popular strategy of authentication.
People usually have a multitude of different passwords and when they create them, they often use a strategy to make it easy to remember [2, 3]. Past studies have shown that users intend to choose weak passwords, which are usually easy to be remembered but vulnerable to be guessed [4, 5]. Also, study reveals that textual passwords are often reused, which have been shown to be an important security threat of passwords [6].
Researchers demonstrated the influence of a person’s environment and exposure to the Internet on their online security behaviour [7, 8]. Password creation strategy, defined as the active approaches that can be used by a password creator to create memorable passwords [9, 3], also seems to be influenced by a person’s environment. For example, it was identified that students from the United States have a higher risk perception toward surveillance than students from the United Kingdom [8]. Also, Yang et al. [10] discuss the cultural influence in password choice. They explain the weak passwords strength level of Chinese by the rapid growth of Internet users and e-commerce markets in China. They hypothesize that providers may not have paid enough attention to security issues because of the focus on market expansion. The results of the aforementioned studies suggest that there is a structural difference in cybersecurity habits between countries [11].
The present study aims to explore the various macrosocial elements contributing to the structural difference between countries in users’ choice of password. The contribution of governments to the problem or to the solutions can be evaluated through this assessment. In order to observe countries’ differences, the password strength performance of users will be compared to macrosocial variables that could influence password creation strategy.
Macrosocial Variables Influencings Users
Few studies show evidence that there is a structural difference between countries in password habits (e.g., [11]) but the macrosocial variables influencing it have rarely been directly tested. To explore the different variables that could play a role in password habits, the literature on macrosocial variables influencing the different aspect of technology, like the use of Internet in general, is considered. Several macrosocial elements might be taken into consideration when evaluating the reasons why users have different levels of performance according to their environment. First, if there is a difference in cybersecurity habits between countries, the characteristics of the government might be an element influencing users. Second, the characteristics of the population, which is directly related to users, would also be an element explaining the impact of the environment. Finally, external variables like cyber-attacks and the level of cyberattack victimization of a country might also be a part of the explanation.
Characteristics of the government. The economic aspect of a government might influence Internet habits. Prior studies have found that a country’s economic development level helps predict the use of internet in a society [12]. Gross domestic product (GDP) is the most closely watched and important economic indicator and considers different variables about a country’s economy, including its consumption and investment [13, 14]. It could be hypothesized that economic indicator would influence not only the use of internet, but other habits related to them.
Along with the economy, the investment and the commitment of countries to cybersecurity is an important variable to consider as the relation is more direct. Researchers have found that when a country invests and commit into the cybersecurity sector, the annual losses due to cybercrime over the country’s Gross National Income decreases [15]. The investments in cybersecurity can include education and tools to help users to more efficiently manage their Internet use.
Characteristics of the population. Digital skills and the overall ability to use the internet are two elements that are directly linked to literacy. Internet users are reading expository text in a hypertext format where ideas are connected by links, headings, icons, and graphics; those elements necessitate similar reading strategies as those used with print text reading [16]. In other words, to seek, evaluate, and use information found on the Internet, readers must navigate through Internet text and apply their knowledge of the reading process. To understand correctly what a password is and to write one, people need to read. Research has shown that password security practices typically conflict with general usability principles [17]. The challenges faced by low-literacy users when creating and managing passwords are likely to extend beyond those experienced by the public. Literacy level affects password habits [18]
External events: Data breaches. According to the Identity Theft Resource Centre’s Annual Data, there were 1862 data breaches in 2021. Researchers have shown that the United States was highly represented in data breaches, and they explain this by their high level of economic activity as well as by their relatively high notification rates they have compared to other countries [19]. Luxemburg, Canada and Great Britain follow the United States in the list of countries most affected by data breaches [19]. When calculating the country-based probability variable, another study shown that France and Brazil have relatively higher probability of data breaches than the other countries [20]. Researchers state that the probability of a data breach is influenced by the country in which it happens [20].
There seems to be a relationship between the influence that data breaches might have on users and their habits. Campbell et.al. [21], examined the stock market reaction to newspaper reports of information security breaches at 38 publicly traded U.S. corporations during the period January 1, 1995 to December 31, 2000. Among the 43 different events, the authors found a highly significant negative market reaction to information security breaches involving unauthorized access to confidential data. Moreover, in their study on 6,000 users from the United States, after a data breach notification, victims changed their password or PIN (51%) or switched to a new account (24%) [22]. The literature suggests that users actively assess the consequences of breaches and react accordingly.
Aim of the study
Users’ habits in relation to cybersecurity is frequently examined from the micro perspective, using survey results to obtain impactful variable from individuals, focusing on usability and security factors of passwords [23, 24]. In this paper, the influence of macrosocial elements on password strength1 is studied in order to offer a global comprehension of the influence of the environment on users. Exploring the different concept of technology and their flaws at the country level encourages future development of new technologies and improve related capital investments (e.g., [28, 29]).
A descriptive analysis of leaked lists of passwords in 2021 is conducted to determine which macrosocial variables would be included in the model and therefore play a formative role in how users formulate their passwords across countries. Then, a prediction model help identify the extent to which variables influence password strength. This study is innovative as it allows to investigate trends in password formulation with regard to social context. The impact of our study is a move toward a better understanding of human behaviour in the context of password formulation specifically, to enable the future crafting of more targeted cybersecurity interventions that would lead to positive online behavioural change.
Method
Sample
Each year, the company NordPass release a list of the 200 most common passwords by country. The list of passwords is compiled using the many cybersecurity incidents (data breaches containing users’ password) that occur in 2021. In total, the list rose from 4 terabytes of information and contain 49 countries. The complete list of countries can be found in Appendix A.
The list comprises between 169,656 and 146,837,497 users’ account per country. The average time to crack passwords is 2082684.368 seconds (range from 0 to 3,214,080,000 seconds). The majority of passwords included in the list can be cracked in less than a minute (61%). The fact that the mean time to crack a password is high in a country means that high quality passwords were included in the 200 most commonly used: the password can be common, but the overall strength is high.
Measures
In order to account for the strength of passwords, the mean time to crack the password, which was already included in NordPass passwords list, was observed. Then, several macrosocial variables have been considered to create a model explaining the level of password strength. A total of 29 different measures have been scrutinized in the exploration of possible model explaining performance of countries in password strength. In order to maintain a low risk of overfitting in the model, a limited number of variables can be inserted in relation to the number of cases (49 countries). The literature reports that one predictive variable can be studied for every ten events (i.e., number of countries) [30, 31]. The complete list of measures that have been considered can be found in Appendix B. In order to determine the five variables to be entered in the model, the first step was to do a correlation matrix. This allowed to avoid highly correlated variables to be entered the model together. Then, different models were tested using an amalgam of variables from the list with a special attention to the important aspect identified in the literature review. The contribution of the variable to the model were very stable and most of them have been chosen because they were predicting password strength. The five variables chosen to enter the final model are named and defined below.
Voice & Accountability (2020). It is one of six components of governance indicator as stipulated by the World Bank. It reflects perceptions of the extent to which a country’s citizens are able to participate in selecting their government, as well as freedom of expression, freedom of association, and a free media.
Global Cybersecurity Index (2020). The Global Cybersecurity Index (GCI) is a trusted reference that measures the commitment of countries to cybersecurity at a global level and is composed of 25 indicators that monitor and compare the level of the cybersecurity commitment of countries with regard to the five pillars – (i) Legal Measures, (ii) Technical Measures, (iii) Organizational Measures, (iv) Capacity Development, and (v) Cooperation – and then aggregated into an overall score. It represents the most comprehensive measures of cybersecurity commitment of countries compared to many other measures that are published by corporations [15].
Cybersecurity Exposure Index (2020). The Cyber Exposure Index is based on data collected from publicly available sources in the dark web and deep web and from data breaches. From this data, signs of sensitive disclosures, exposed credentials and hacker-group activity against companies are identified.
Literacy (2022). This measures the percentage of adults in a country who are able to read and write their common language. A higher literacy rate is an indication of higher standards of education and the good ability of the population to find formal employment.
GDP per Capita (2020). Gross domestic product (GDP) is the standard measure of the value added created through the production of goods and services in a country during a certain period. As such, it also measures the income earned from that production, or the total amount spent on final goods and services (fewer imports).
Analysis
Multiple linear regression (MLR), also known simply as multiple regression, is a statistical technique that uses several explanatory variables to predict the outcome of a response variable. Multiple regression is an extension of linear regression that uses just one explanatory variable. MLR assumes that there is a linear relationship between the dependent variable and the independent variables. It also assumes that the data should not show multicollinearity, which occurs when the independent variables (explanatory variables) are highly correlated. The amount of error in the residuals is similar at each point of the linear model, the observations should be independent of one another and occurs when residuals are normally distributed [32]. All those assumptions have been tested through data observation. The software IBM SPSS 28 was used to do the analysis.
Results
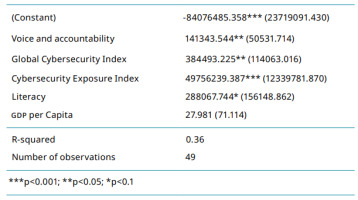
Multiple linear regression was used to test if the five macrosocial variables under study significantly predicted password strength. The overall regression was statistically significant (R² = 0.36, F = 23.46, p = < 0.004). The model is presented in Table 1.
It was found that Voice and accountability (β=141343.544, p=0.008), Global Cybersecurity Index (β=384493.225, p=0.002), Cybersecurity Exposure Index (β=49756239.387, p=0.000), and level of literacy (β=288067.744, p=0.072) significantly predicted password strength. It was also found that the GDP per capita (β=27.981, p=0.696) did not significantly predict password strength.
Discussion
The analysis of the present study help identifies a variety of different macrosocial measures significantly predicting password strength of users: literacy, voice and accountability, level of global cybersecurity, and the level of cybersecurity exposure. Considering past literature on the subject, one variable was surprisingly not associated with an increase password strength, that is, the GDP per capita. Each of those measures are presented in this section in the light of previous work through broader categories: Characteristics of the government, characteristics of users and external variables.
Characteristics of the Government
Freedom in a country has shown to have an impact on Internet use. Voice and accountability indicator reflects perceptions of the extent to which a country’s citizens are able to participate in selecting their government, as well as freedom of expression, freedom of association, and a free media. Researchers suggest that greater levels of Internet diffusion are associated with greater levels of voice and accountability [33, 34]. Musa et al. [35] argue that developing countries are more resistant than developed countries to the introduction of technologies that can be used to fight corruption, such as Internet-based technologies. Beyond the use of internet, the impact of freedom is seen on cybersecurity. A strong positive association has been shown between Cybersecurity Capacity Scale and cross-national indicators of citizen perceptions of having voice and accountability [36]. The result of the present study confirms the impact of voice and accountability on password performance as this variable is a good predictor of password strength.
The adoption of technology in a country has been proven to be impacted by many factors including its economic development and growth [37]. Compared to more developed countries, countries that are less developed possess inferior infrastructure, less effective manpower (partly because of low education levels), and business models that have not shifted from the industrial age to the information age [38]. The wealth disparity has also been noted to impact technology adoption, although previous studies have examined the wealth disparity from a micro level [39 – 42]. The result of the present study indicates that wealth disparity does not influence the strong password hygiene as GDP was not significantly predicting password strength. This result might be explained by the sector in which developed countries invest but also other influencing variable like experience in the IT sector. Past studies have shown that countries need to acquire experience with IT before investments begin to reward the country economically [43]. Benefiting from resources is not enough to explain effective use of technology.
Even if the GDP is not a significant element in citizen password strength, the level of investment of a government in cybersecurity has an impact on security of users. The Global Cybersecurity Index (GCI) is a trusted reference that measures the commitment of countries to cybersecurity at a global level. Researchers have found that as the score for the Global cybersecurity increases, the annual losses due to cybercrime for each country over their Gross National Income decreases [15]. The literature shows that commitment of countries to fight against cybersecurity is profitable economically. The present study goes further by showing the impact on users by demonstrating that this type of investment predicts better password strength performance.
Characteristics of Users at a Macro-Level
Literacy is an important aspect to consider in this study as it is directly connected to the use of technologies. To seek, evaluate, and use information found on the Internet, readers must navigate through Internet text and apply their knowledge of the reading process [16]. Today’s definition of literacy is being broadened to include “literacy skills necessary for individuals, groups, and societies to access the best information in the shortest time to identify and solve the most important problems and then communicate this information” [44]. Most knowledge of late trends on technology is acquired by information found on the Internet. Because bei;00ng knowledgeable is closely related to the capacity to acquire this knowledge (e.g., being able to read), people with low level of literacy can hardly adapt. The challenges faced by low-literacy users when creating and managing passwords are documented and research indicates that they are higher than the general population [18]. Research shows that when users’ level of cyber security knowledge increases, so does their cybersecurity behaviour contributing to good hygiene [45]. However, if users are not able to get this information about cybersecurity because of their inability to read, their security will be impacted. The results of the present study are therefore not surprising: when the level of literacy of a population increases, the strength of passwords also increases.
External Variables Influencing Countries
The results show that the number of cybersecurity incidents exposure of a country is positively associated with password change. The more a country is under attack, the more people use strong passwords. This suggests that people might be sensible to the importance of protecting data with strong passwords when they are exposed to more cybersecurity incidents. Users are well aware of the meaning of a data breach [46], and it influences their behaviour. For example, there is a highly significant negative market reaction to information security breaches involving unauthorized access to confidential data [21]. In their study on 6,000 users from the United States, after a data breach notification, victims changed their password or PIN (51%) or switched to a new account (24%) [22]. Users are also recognized to be comfortable with proactive password resetting in the event of reuse and sharing information with other identity providers [46]. Therefore, users are aware of what will protect them and are more likely to do it when they are increasingly exposed to incidents. This demonstrates the resilience of users when they live in hostile environment but also the importance of making this information public as this knowledge is a protective factor for users. Mandatory reporting of data breaches introduced in Canada in 2018 [47] might be contributing solution to protect users.
Limitations
The set of data taken from Nordpass present important limitations as the method used to estimate the time to crack is unspecified. The list was investigated because the mean time to crack appears to be high. Some passwords from the list were weak (e.g., kallynlavallee) but were associated with a cracking time of more than 100 years. This is considered an important limitation of the dataset. However, the unspecified method is used consistently across the countries. Therefore, the metric could be used for the comparative analysis as it is consistent and can be relied upon.
Also, this study takes into consideration a macro perspective of the password strength, but a myriad of element can influence users’ choices. The objective of the present study was to explore the influence of different large-scale policies and not individuals’ decisional process.
Conclusion
The present study helps understand the importance of macrosocial variables on predicting password strength of users. It points toward the fact that some characteristics of the government influences password strength performance of users. For example, democratic countries and countries in which the government invests in cybersecurity increase the password performance of users. The economic commitment of countries to fight against cybersecurity has been proven to be profitable economically and this study show that it is also associated with password strength of their citizens. Government has an important role to play on the cyber-protection of users whether it is direct (by investing in cyber security) or indirect (by prioritizing democracy and education).
Another important element raised by the present study is that exposure to data breaches increases the strength of user’s password. This can be explained by the fact that the population adapt to the threat and this behaviour point toward the importance of mandatory reporting of data breaches by organizations. If they are confronted to mandatory reporting, users are more likely to know about the breaches and continue to adapt their behaviour and it becomes a protection factor.
Through a better understanding of human behaviour in the context of password formulation, our research focuses on identifying common denominators in behaviour that can lead to increased user vulnerabilities in online password formulation. The novelty of our exploratory research lies in our attempt to understand macrosocial variable associated with cybersecurity. The implication of this study concerns the development of policies around cyber security configurations and investment set by nations and institutions.