1. Introduction
Energy security is one of the most important pillars of modern society and the main pillar of stability of every country. Energy infrastructure is a part of critical infrastructure and represents, as its name suggests, a critical point of national security, since it is always a potential target for cyber warfare, cyber terrorism, or financially motivated cyberattacks [1–4]. As the energy industry is enhancing, developing, and digitalising, cyber threats are becoming bigger issues for energy infrastructure [5, 6]. Energy infrastructure is susceptible to cyberattacks, which pose a serious threat to the energy sector as a whole. These cyberattacks can lead to operational disruptions, financial losses, and may even jeopardise national security. The integration and digitalisation of Smart Grid technology has made energy infrastructure more susceptible to cyberattacks. Since the Smart Grid relies heavily on information and communication technologies, it has become an attractive target for cyber threats [7–10]. As a result, the security of energy supply is further jeopardised by the vulnerabilities associated with the Smart Grid technology. There are different types of cyber threats that target specific vulnerabilities in the energy system. Many threats can exploit a specific vulnerability, and a specific vulnerability can be a target for a particular cyber threat within the energy.
In the recent decade, the energy sector and energy infrastructure globally have suffered numerous high-profile cyberattacks. The best-known attack happened in 2010 at the Natanz nuclear facility in Iran, and it is considered the very first known malware (named Stuxnet) specifically constructed to damage physically critical infrastructure by exploiting Siemens Supervisory Control and Data Acquisition (SCADA) systems to sabotage centrifuges [11–13]. Stuxnet manipulated centrifuge frequencies, causing them to speed up and slow down until they failed. During this process, the system displayed normal data to avoid detection. As a result, approximately 1000–5000 centrifuges were damaged. Stuxnet was the first cyberattack to reveal vulnerabilities in SCADA systems [11–13]. Two years later, in 2012, the Shamoon malware attacked Saudi Aramco, causing the deletion of thousands of workstations and the loss of valuable data [14–17]. Saudi Aramco is one of the biggest oil companies in the world. Shamoon malware was not created to target control systems like SCADA. Instead, it was designed to delete hard disk data, rendering computers unable to start [14–17]. In 2015, the BlackEnergy malware caused power outages across Ukraine, and in 2016, the Industroyer/CrashOverride malware targeted grid control protocols in Ukraine [18–22]. BlackEnergy malware targeted three Ukrainian energy companies and it was injected by spear-phishing emails. After infiltration in the system, the malware deleted all the data from the computer systems, and SCADA systems were turned off, which caused a break in energy distribution across the country [23–26]. About 225,000 people were left without electricity for several hours in the winter period. This was the first cyberattack that caused a physical interruption of electric power. In the Industroyer/CrashOverride attack in 2016, the target again was an energy company in Ukraine. The malware was specifically designed to manipulate industrial protocols (IEC 60870-5-101, IEC 60870-5-104, and IEC 61850), which are used in power grids, and its goal was manipulating grid control protocols. Industroyer is considered the most sophisticated cyberattacks on the energy infrastructure after Stuxnet [23–26]. Another well-known example of a cyberattack targeting energy sector happened in 2017 in Saudi Arabia. This malware, known as Triton/Trisis, was designed to attack the Safety Instrumented Systems (SIS) at a Saudi petrochemical plant [27, 28]. The goal was to destroy physically the infrastructure of the plant. Malware was designed for the sabotage of the SIS and it is the only known cyberattack so far that directly targeted the safety systems of industrial control networks (protection systems). In this case, the attack did not fully succeed, because the malware caused an unintended shutdown of the system, which led engineers to discover the problem [27–29]. If the attack had succeeded, it could have led to a massive explosion or an industrial incident with human casualties. The very fact that the safety systems were the target was a precedent in the cyber security of critical infrastructure [27, 28]. In 2021, the Colonial Pipeline ransomware attack in the United States caused fuel supply disruptions along the East Coast [30–32]. The DarkSide ransomware was designed as a form of financial blackmail and was financially motivated [18, 33]. The attackers exploited compromised virtual private network (VPN) credentials that did not have multi-factor authentication (MFA), and the attack caused 6 days of shutdown of the main pipeline. After infiltration, they deployed ransomware that locked the IT systems (billing and business networks) [18, 31–33]. All of these incidents and cyberattacks exploited specific vulnerabilities in the systems in order to penetrate and infect them.
This research systematically explores cyber threats in the energy sector with a specific focus on Smart Grids. This paper examines both cyber threats and possible vulnerabilities within the Smart Grids and energy sector in general. The existing literature primarily focuses on either cyber threats in the energy sector and smart grid or vulnerabilities within these areas. The focus in the literature is usually on the type of the threats and rarely on the vulnerability with clear fragmentation between concepts of threats and vulnerability. Nevertheless, being able to understand the potential correlations between vulnerabilities within the Smart Grid and cyber threats is crucial for constructing an effective defence system. It is logical to expect that vulnerabilities in any system reduce its security. Likewise, certain vulnerabilities within the Smart Grid can be exploited by cyber threats. For instance, whenever a specific type of cyber threat is discussed in the literature, it is usually accompanied by a vulnerability that creates an opportunity for that threat to occur. Correlations between vulnerabilities and cyber threats mean vulnerabilities that lead to cyber threats and can be identified and prevented more effectively. This research conducts a systematic literature review in order to explore the relationships between the vulnerabilities inherent in Smart Grid systems and the potential cyberattacks on their infrastructure. To address this gap, a systematic literature review was conducted following the preferred reporting items for systematic reviews and meta-analyses (PRISMA) guidelines. The objectives were to identify the most frequently reported threats and the most critical vulnerabilities, and to map their interdependencies. Mapping threats to vulnerabilities in this paper offers a unified perspective and insights that directly contribute to improving the security and defence of Smart Grid architecture as it is the first attempt in the literature to systematically map cyber threats to corresponding vulnerabilities in the energy sector.
2. Methodology
There has been a substantial amount of research on cyber threats and vulnerabilities within the Smart Grid and the broader energy sector, as this topic is critical to security studies. Most of the studies are focused exclusively on either cyber threats or system vulnerabilities, exploring them separately and without examining potential correlations. Consequently, there is a significant and evident gap in the research concerning studies that explore the potential correlations or dependencies between cyber threats and vulnerabilities in the Smart Grid.
Two research questions were defined for this paper:
Q 1. What are the most commonly mentioned types of cyber threats targeting the Smart Grid in the existing literature?
Q 2. What are the most critical vulnerabilities exploited in cyberattacks against energy infrastructure in the Smart Grid?
A thorough literature review was conducted to address two research questions, following a clearly established review protocol. For illustrating the gap in the literature regarding studies that focus on both threats and vulnerabilities, a bibliometric analysis was conducted. As a part of bibliometric analysis, the co-occurrence network of keywords in the reviewed literature was created using R, a programming language widely used for statistical computing and data analysis, using the Biblioshiny interface and the Bibliometrix package. The co-occurrence network of keywords in the reviewed literature is presented and explained in the Results section.
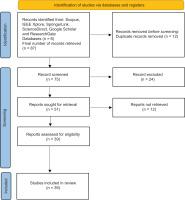
A systematic search was performed searching the literature in six online databases: Scopus, IEEE Xplore, SpringerLink, ScienceDirect, Google Scholar, and ResearchGate. The inclusion criteria were: peer-reviewed journal and conference papers, publications in the time range of 6 years (2018–2025), studies that focus on cyber threats in energy and Smart Grids, studies that focus on vulnerabilities within the Smart Grid or energy sector, studies that address both cyber threats and vulnerabilities of the Smart Grid. This study focused on the last 6 years of publication in order to examine the most recent literature in the field of cybersecurity in the energy sector. Since the field of cybersecurity is developing very fast, it is important to include the most recent studies in order to get correct analysis. Exclusion criteria were: studies not related to the energy sector, opinion pieces, editorials, or blogs, and duplicate records. The process of systematic literature review consisted of three steps: identification phase, screening phase, and inclusion phase. The systematic literature review in this paper was conducted following the PRISMA guidelines [34]. Figure 1 presents the visual representation of the PRISMA flow diagram that was used for the identification phase, screening phase, and inclusion phase of the literature review.
Initially, a total of 87 studies were collected using the following keywords: smart grid, cyber threats, vulnerabilities of smart grid, and energy sector. From the initial 87 collected studies, 12 studies were excluded in the identification phase because they were duplicates, leaving 75 records for the next phase. As it is presented in the Figure 1, in the following screening phase, 24 records were excluded because they did not fully align with the inclusion criteria. The following step was a full-text review of the selected papers, and in this step 12 records were excluded because they did not fully align with the inclusion criteria. In the final step, 39 studies were included and the literature review was conducted on 39 studies that are presented in Table S1 in the Appendix. The findings were analysed through qualitative synthesis to identify key trends, gaps, and recurring themes in the literature. The selection of these papers was based on their direct relevance to the objective of this research and on inclusion rules. While this study is based on a systematic review of 39 publications that met the defined inclusion criteria, additional literature was consulted to provide broader context and to frame the research problem. Together, these papers provided a comprehensive, multidisciplinary perspective on the cybersecurity challenges, threats, and vulnerabilities confronting the energy sector.
A data extraction table (Table S1 in the Appendix) for 39 selected studies was created to capture the following elements for each study:
3. Results
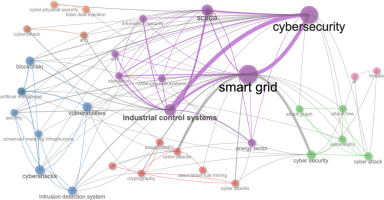
In the Results section, the results of the literature review and bibliometric analysis are presented. When it comes to the analysed literature, most of the existing papers treat cyber threats and system vulnerabilities as separate domains. They either categorise types of attacks or list common weaknesses of the Smart Grid infrastructure, but rarely investigate how specific vulnerabilities are exploited by particular cyber threats. This lack of integrative analysis limits the practical applicability of the existing findings for operators who need to prioritise security investments. Figure 2 illustrates the co-occurrence network of keywords in the reviewed literature. The co-occurrence network of keywords is a bibliometric visualisation that shows how the keywords from the analysed literature co-occur together (in the same papers). The stronger the connection between clusters, the more frequently the terms that co-occur in the reviewed literature, indicating a closer conceptual or thematic relationship. This co-occurrence network visualisation was generated in R, a programming language widely used for statistical computing and data analysis, using the Biblioshiny interface and the Bibliometrix package.
The co-occurrence network visualisation (Figure 2) highlights the fragmented nature of the existing research on Smart Grid cybersecurity and clearly illustrates the gap that this study addresses. As it is presented in Figure 2, the most dominant cluster in the analysed literature is the purple cluster that connects ‘Smart Grid’, ‘cybersecurity’, ‘SCADA’, and ‘industrial control system’. The purple cluster represents that the majority of the literature is focused on the general security challenges of critical infrastructure without linking those threats to specific vulnerabilities. The second cluster is the blue cluster that connects ‘blockchain’, ‘artificial intelligence’ (AI), ‘cyberattacks’, and ‘intrusion detection systems’. The blue cluster represents a technology-based cluster that emphasises the importance of the vulnerabilities and new modern technologies such as blockchain and AI, but without strong integration into the broader Smart Grid security component. The third cluster is the green cluster centred around ‘attack graph’, ‘attack tree’, and ‘vulnerability’. The green cluster is based more on a methodological focus and disconnected from real-world incidents and empirical validation. Smaller clusters are the red clusters (connecting ‘cryptography’, ‘accountability’, and ‘association rule mining’) and the pink cluster (connecting ‘AI’ and ‘threats’), and these two represent subfields that are still isolated from the bigger clusters, which means that they are still in development. The biggest three clusters (the purple cluster, the blue cluster, and the green cluster) are not densely connected with each other and there is evidently no coherent bridge that systematically maps how vulnerabilities correspond to different threat vectors across technical, methodological, and applied dimensions. From Figure 2, the fragmentation of the existing literature is clearly visible, together with the gap in the literature that tends to examine threats or vulnerabilities separately but rarely integrates them with empirical evidence of attacks, which is precisely the contribution of this study.
In order to present the answer to two research questions, Tables 1–3 were created. The tables are based on the original literature review that is presented in Table S1 (Appendix). Table 1 displays the number of occurrences (number of times mentioned in the literature) of various cyber threat types. Table 1 describes all the types of cyber threats within the energy sector and Smart Grid environment that are described in the literature. The first column of Table 1 lists the specific types of cyber threats, while the second column explains the type of the threat and gives a concrete example from the real incidents that happened in the world (if applicable). The third column indicates the frequency at which each threat is mentioned. References from the literature cited are included in the third column of Table 1. This table answers the first research question of this paper:
Table 1
The most common types of cyber threats in the Smart Grid.
| Cyber threat type | Explanation and example of the threat | Frequency of occurrences in the literature | References |
|---|---|---|---|
| Malware | Malicious software used to infiltrate, damage, or disrupt systems. Example: Stuxnet exploited Siemens SCADA systems of the nuclear plant to sabotage and compromise centrifuges at Natanz [11–13]. | 7 | [7, 8, 35–39] |
| Denial of Service (DoS); DDoS | Attackers overload systems or communication channels, making services unavailable. Example: Attackers disrupted SCADA and power distribution systems, which lead to power outage in Ukraine 2015 blackout [18, 21, 25]. | 7 | [5, 35, 40–44] |
| Spoofing; Sybil; jamming | Spoofing is falsifying or disguising an identity. Sybil is a creation of multiple fake identities within a network. Jamming is disrupting or interfering with communication. Example: Manipulating with signals in order to mislead operators and cause power blackout. | 3 | [45–47] |
| Other (cross-site, blockchain, etc.) | Attacks in this category are less known, but also dangerous. cross-site attacks that target web-based control platforms and blockchain-based vulnerabilities. These attacks usually exploit smart contracts or insecure dashboards. Example: Cross-site scripting on web-based SCADA dashboards. | 4 | [44, 48–50] |
| Advanced persistent threats (APTs) | Long-term stealthy campaigns using phishing and credential theft. ATP highly sophisticated cyberattacks, usually carried out by state-sponsored hacker groups or well-organised criminal groups. | 4 | [6, 43, 51, 52] |
| Insider threats | Authorised employees misuse access or credentials. Example: Shamoon in Saudi Aramco in 2012, helped by weak insider policies. | 3 | [52–54] |
| Cyber-physical attacks; sabotage | These attacks are targeting physical processes and safety systems. Example: Triton/Trisis attempted to disable SIS in Saudi Arabia [14–17, 27, 28, 55, 56]. | 3 | [47, 57, 58] |
| Data breaches/falsification | Attackers in the Stuxnet attack did not only sabotaged centrifuges, but they also made sure that operator displays correct data in order to camouflage the damage and the attack, showing how manipulated data can hide physical sabotage [11–13]. | 4 | [8, 35, 38, 46] |
| Unauthorised access | Gaining entry via weak authentication or exposed systems. Example: Colonial Pipeline - compromised virtual private network (VPN) creds without multi-factor authentication (MFA) [18, 30–33]. | 3 | [7, 52, 59] |
| Man-in-the-middle (MitM) | Intercepting and altering communications. Example: BlackEnergy in Ukraine manipulated grid commands [18, 20, 21, 25, 60]. | 3 | [41, 54, 59] |
| Ransomware | Encrypting information technology/operation technology (IT/OT) data and demanding ransom in order to encrypt data. Example: Colonial Pipeline caused a 6-day fuel disruption [18, 30–33]. | 2 | [40, 61] |
| Injection/packet injection | Malicious commands injected into control traffic. Example: Industroyer manipulated IEC protocols to trip breakers [18, 20, 21, 25, 60]. | 2 | [42, 62] |
| Botnets | Botnet is a hidden network of infected computers remotely controlled by hackers to launch large-scale attacks. Shamoon malware in Saudi Aramco was spread mimicking botnet-like propagation. Because of the botnet style of operating malware was enabled automatic replication throughout the network, data erasure, and large-scale system disruption [14, 15–17, 55, 56]. | 2 | [59, 61] |
| Firmware threats/exploitation | Stuxnet malware was designed to alter Siemens PLC firmware in order to sabotage the performance of the centrifuges at Natanz [11–13]. Triton/Trisis malware attacked Schneider Electric Triconex safety controllers with the intention of disabling Safety Instrumented System [14–17, 55, 56]. | 1 | [63] |
| Phishing | Phishing email enabled the BlackEnergy malware to spread during Ukraine 2015 power grid attack, allowing for malware to access the SCADA system [18, 20, 21, 25, 60]. | 1 | [40] |
| Zero-day attacks | Industroyer malware in Ukraine exploited previously unknown vulnerabilities in industrial communication protocols (e.g., IEC 61850 and IEC 60870-5-104) and caused power outages [18, 20, 21, 25, 60]. | 1 | [64] |
Table 2
The most critical vulnerabilities addressed in cyberattacks aiming the Smart Grid.
| Critical vulnerability type | Explanation and example of vulnerability in the system | Frequency | References |
|---|---|---|---|
| Insecure; weak protocols; communication | Many ICS/SCADA protocols (e.g., Modbus, DNP3, and IEC 60870) lack built-in authentication/encryption/verification, enabling exploitation of the protocols. Example: exploited in BlackEnergy (Ukraine 2015) to shut down breakers [18, 20, 21, 25, 60]. SCADA components exposed online or with weak protocols. Example: Industroyer (2016) exploited IEC 61850/104 protocols to trip breakers [18, 20, 21, 25]. | 11 | [8, 35, 37–39, 45, 47, 59, 65–67] |
| Legacy systems; outdated software; hardware | Old operating systems and control devices no longer receive patches, leaving them exposed. Example: Stuxnet malware targeted outdated Siemens PLC firmware at Natanz [11–13]. | 7 | [6, 8, 37, 48, 50, 59, 68] |
| Lack of encryption; poor encryption | Lack of protocols and communication encryption enabled Ukraine power grid attacks in 2015 and 2016. Attacker exploited unencrypted IEC 60870 protocols and caused power outage [18, 20, 21, 25, 60]. Also, in Stuxnet attack, unsecured PLC communications were exploited in order to inject the malware [11–13]. Triton/Trisis malware exploited weak protective layers in safety controllers to sabotage the protection [15, 17, 55]. | 4 | [45, 47, 65, 67] |
| Weak authentication; access control | Default or shared passwords, lack of multifactor authentication (MFA) make systems easy to breach. Example: Colonial Pipeline compromised VPN credentials without MFA [11–13]. | 5 | [35, 36, 39, 45, 51] |
| Lack of standardised controls; governance gaps | Inconsistent security policies and lack of global cybersecurity standards weaken resilience of the energy sector. Example: Shamoon malware spread widely due to weak governance of endpoint security at Saudi Aramco [14–17, 55, 56]. | 3 | [66, 69, 70] |
| Policy; strategy gaps; insufficient plans | Lack of or weak national or sectoral cyber strategies leave operators unprepared on a national level. Example: Ukraine in 2015 did not have coordinated national cyber defence, which ultimately enabled the malware to penetrate the grid [18, 25]. Furthermore, because of the weak contingency planning and lack of response mechanisms, ransomware exploited the weakness and attacked Colonial Pipeline [30, 32]. | 3 | [40, 69, 70] |
| Insecure; poor network topology; segmentation | Flat networks allow attackers to move from IT to operational technology (OT) environments. Example: Triton/Trisis malware attackers reached SIS controllers due to poor segmentation [14, 15, 17, 27, 28, 55, 56]. | 4 | [8, 37, 39, 57] |
| Firmware; device vulnerabilities | Exploitable flaws in PLC or device firmware. Example: Stuxnet replaced Siemens PLC code to manipulate centrifuge speeds [11–13]. | 2 | [7, 35] |
| IoT integration flaws; insecure internet of things (IoT) | IoT devices in Smart Grids and energy infrastructure do not have security features implemented (strong authentication or patching), which makes them a weak spot. | 2 | [35, 39] |
| Human error; lack of training; awareness | Employees fall for phishing or misconfigure systems. Example: BlackEnergy (2015) initial infection vector via spear-phishing [18, 20, 21, 25]. | 2 | [40, 48] |
| Lack of real-time threat detection; monitoring | Without timely detecting malware or anomalies in the system, advanced persistent threat (APT) is in a persistent presence. Example is Ukraine Industroyer and CrashOverride malware that was undetected when injected and detected after activation, which means malware was in the system undetected for significant amount of time [25]. | 3 | [63, 71, 72] |
| Insufficient endpoint protection | Lack of antivirus or endpoint security leaves IT systems open. Example: Shamoon wiped 30,000 PCs at Saudi Aramco [14–17, 55, 56]. | 1 | [5] |
| Testing and simulation exposure | When testing certain functionality within the system, testing environment must be protected. For example, Colonial Pipeline attack showed how lack of testing, simulations, and preparedness for ransomware attack could be fatal. | 2 | [46, 71] |
| Ethical framework gaps | Lack of norms and laws around critical infrastructure cyber defence. Example: Policy debates after Stuxnet highlighted legal and ethical gaps in cyber warfare [11–13]. | 1 | [40] |
| Lack of resilience; redundancy | No backup systems for critical operations. Example: Ukraine 2015 blackout showed how lack of redundancy worsened outages [18, 20, 21, 25]. | 1 | [35] |
| Chip-level hardware vulnerabilities | Exploitable failures at hardware/firmware level. Example: Stuxnet malware altered Siemens PLC firmware in order to sabotage centrifuges at the power plant [11–13]. | 1 | [50] |
Table 3
Mapped critical vulnerabilities and corresponding cyber threats with the real-world cyberattack examples.
| Cyber threat | Mapped critical vulnerabilities | Mechanism of exploitation | Real-world case example |
|---|---|---|---|
| Malware | Insecure protocols [8, 35, 37–39]; weak authentication [35, 36, 39]; firmware/device vulnerabilities [7, 37]; legacy systems [8, 37]; poor segmentation [8, 37, 39]; insecure IoT [35, 39]; lack of redundancy [35] | Exploits unpatched SCADA/ICS or outdated operating systems (spreading via weak authentication and outdated PLC firmware) | Stuxnet (2010) – sabotaged Natanz centrifuges via Siemens SCADA/PLC [11–13] |
| Denial of service (DoS/DDoS) | Weak protocols [35, 40, 42, 43, 44]; policy gaps [40, 70]; governance gaps [66, 70]; human error [40]; testing exposure [46, 71] | Flooding protocols like Modbus/DNP3 channels; exploiting lack of redundancy | BlackEnergy (Ukraine 2015) – SCADA shutdown and power outage [18, 20, 21, 25, 60] |
| Spoofing/jamming | Weak protocols [45, 47]; poor encryption [45, 47]; weak authentication [45]; testing exposure [46] | GPS spoofing; falsified grid synchronisation signals | Stuxnet created false data displayed on Human-Machine Interface (HMI) in order to maintain hidden and in order not to be detected [11–13]. |
| Other (XSS, blockchain flaws) | Legacy systems [48, 50]; human error [48]; governance gaps [66, 69]; policy gaps [69] | Cross-site scripting on SCADA dashboards; smart contract flaws | General ICS/blockchain risks – less linked to major outages |
| Advanced persistent threats (APTs) | Weak authentication [36, 51]; legacy systems [2]; SCADA protocol flaws [6, 70]; weak protocols [35, 39] | Long-term infiltration via spear-phishing, credential theft | Industroyer (2016) – automated manipulation of IEC 61850/104 [18, 20, 21, 25, 60]. |
| Insider threats | Weak authentication [51]; policy gaps [40]; governance gaps [69] | Employees exploiting access rights, lack of monitoring/logs | Shamoon (2012) – internal spread, 30,000 PCs wiped in Saudi Aramco [14–17, 55, 56]. |
| Cyber-physical attacks/sabotage | Poor segmentation [37, 57]; SCADA exposure [6, 70]; weak protocols [47] | Manipulation of safety systems | Triton/Trisis (2017) – targeted Triconex SIS, risk of explosion [14–17, 55, 56]. |
| Data breaches/falsification | Weak protocols [8, 38]; weak authentication [35]; poor encryption [47, 65] | Intercepting grid communication; falsifying data | Stuxnet (2010): falsified centrifuge data, so operators saw normal values while sabotage occurred [11–13]. |
| Unauthorised access | Weak authentication [35, 52]; legacy systems [59]; SCADA flaws [59] | Remote access abuse through default passwords or outdated VPNs | Colonial Pipeline (2021)– VPN creds without MFA and ransomware shutdown [18, 30–33] |
| Man-in-the-middle (MitM) | Weak protocols [41, 54]; weak authentication [45]; SCADA flaws [59] | Intercepting and altering grid commands | BlackEnergy (2015) – adversaries manipulated breaker commands [18, 20, 21, 25, 60]. |
| Ransomware | Weak authentication [40]; policy gaps [40] | Encrypting IT/OT data, ransom demand | Colonial Pipeline (2021) – DarkSide ransomware disrupted fuel supply chain [18, 30–33]. |
| Injection/packet injection | Weak protocols [42, 62] | Malicious commands injected into control traffic | Industroyer (2016)– injected packets into IEC protocols to trip breakers [18, 20, 21, 25, 60]. |
| Botnets | Weak authentication [59, 61] | Using insecure IoT devices for DDoS | Shamoon (2012): spread rapidly across 30,000 systems, mimicking botnet-like propagation through worm-style replication explosion [14–17, 55, 56]. |
| Firmware exploitation | Device vulnerabilities [7, 35, 63]; chip-level vulnerabilities [50] | Exploiting firmware flaws or supply-chain tampering | Stuxnet (2010): modified Siemens PLC firmware to alter centrifuge operations [11–13]. |
| Phishing | Human error [40] | Employees deceived into clicking malicious links that were entry vector for APTs | BlackEnergy (2015) – initial spear-phishing compromise [18, 20, 21, 25, 60]. |
| Zero-day exploits | Lack of real-time detection [64] | Exploiting unknown flaws before patches exist | Industroyer (2016): exploited previously unknown flaws in industrial communication protocols (IEC 61850 and IEC 60870-5-104) to trip breakers [18, 20, 21, 25, 60]. |
Q 1. What are the most commonly mentioned types of cyber threats targeting the Smart Grid in the existing literature?
The most common types of cyber threats targeting the Smart Grid include: malware, denial of service (DoS); distributed denial of service (DDoS), advanced persistent threats (APTs), cross-site, data breaches, spoofing, Sybil attacks, and jamming. Malware and DoS are mentioned for seven times, APTs, cross-site, data breaches are mentioned for four times, and spoofing, Sybil attacks, and jamming are mentioned thrice each in total, which indicate that malware and DoS are the most common cyber weapons used.
Table 2 lists all the vulnerabilities of the systems that are encountered in the energy sector and Smart Grid. This table shows the number of occurrences of different vulnerability types. The first column of Table 2 lists the specific types of vulnerabilities in the Smart Grid, while the second column explains the vulnerability in the system, and if applicable, gives an example of the real-world energy system vulnerability that was exploited by the cyber threat. The third column indicates the frequency at which each threat is vulnerable in the reviewed literature. Table 2 answers the second research questions of this paper:
Q 2. What are the most critical vulnerabilities exploited in cyberattacks against energy infrastructure in the Smart Grid?
The most mentioned type of vulnerability in Smart Grids is insecure or weak protocols and communication. The second most mentioned vulnerabilities are legacy systems, and outdated software and hardware. Insecure, weak protocols, and communication are mentioned for 11 times in the review literature, and legacy systems, and outdated software and hardware are mentioned for seven times.
According to the literature, the biggest vulnerabilities that are present in the energy system and that are targeted by the cyber threats are insecure and weak protocols or communication. Industrial protocols are specific, and unlike IT protocols, they were not designed to protect data but to enhance the velocity of performance. The lack of built-in security mechanism, industrial protocols can be easily targeted and exploited. This vulnerability was targeted in the BlackEnergy cyberattack in Ukraine. Insecure and weak industrial protocols, such as IEC 60870-5-104, Modbus, and DNP3, were not originally designed with authentication or encryption mechanisms, which made them highly susceptible to manipulation. A clear example is the 2015 Ukraine power grid attack, in which malware exploited these protocol weaknesses in combination with stolen operator credentials disruption [18, 20, 21, 25, 60]. Unprotected industrial protocol IEC 60870-5-104 enabled the attackers to control substations. The unauthorised commands were sent (‘open breaker’ and ‘close breaker’ commands) to the substations, and the used protocol was not able to detect malicious instructions or to verify the authenticity of the commands that lead to blackouts [18, 20, 21, 25, 60]. This case demonstrates that insecure communication protocols act as an enabler of cyber threats, transforming a credential theft into a large-scale operational disruption [18, 20, 21, 25, 60]. The second biggest vulnerability is legacy system and outdated software or hardware. Usually in the energy infrastructure legacy systems, outdated software and hardware are used for many years (even decades). This is because energy infrastructure and environment (or industrial infrastructure in general) have to work 24×7, without interruptions, and doing update or patch of the system can be very complicated because every system shutdown can be very risky. That is why energy infrastructure is an attractive target for advanced malware [11–13]. A well-known example is the Stuxnet malware attack, which specifically targeted Siemens S7-300 Programmable Logic Controller (PLC) running outdated firmware in the Natanz nuclear facility [11–13]. The attackers exploited multiple zero-day vulnerabilities in Windows systems to successfully infect the malware. The malicious code was injected into PLCs’ firmware. The legacy devices did not have any modern security mechanisms implemented (such as code signing, intrusion detection, or integrity verification), and the malicious malware ran undetected. Stuxnet altered the logic of the centrifuge controllers while simultaneously sending falsified feedback signals to operators, hiding the sabotage. The outdated and unpatched hardware and firmware was the core vulnerability that enabled the attack to succeed [11–13].
Table 3 shows the correlation between vulnerabilities and cyber threats discussed in the reviewed literature. Table S1 of the systematic literature review is available in the Appendix. The first column of Table 3 displays the various types of cyber threats that have been researched in the literature. For each type of cyber threat, there is a corresponding critical vulnerability that enables that specific threat to jeopardise the Smart Grid. The idea is to understand the vulnerability that can be exploited by the threat. The second column contains mapped vulnerability; the third column of the table has the mechanism of exploitation; and the last column gives a real-world example (if it exists for that particular threat or vulnerability). It is important to stress that some of the vulnerabilities overlap across different types of cyber threats. This is because, in the real-world scenarios, different types of energy infrastructure and system vulnerabilities are dependent on each other, meaning that vulnerabilities cannot be definitely segregated from each other. For example, malware, APTs, ransomware, and botnets exploit both weak authentication and insecure protocols, whereas legacy systems and poor segmentation are responsible for both cyber-physical sabotage and data breaches. An important conclusion that can be drawn from Table 3 is that one type of cyber threat can exploit more than one vulnerability. This again means that if one vulnerability is taken under control, more than one threat can be neutralised. Table 3 also shows the exact mechanisms through which vulnerabilities enable specific attacks. Mapping of vulnerabilities and cyber threats in Smart Grid and energy infrastructure proves that a relatively small set of critical vulnerabilities enables multiple cyber threats, which is again underscoring the need for integrated and systemic defence strategies. For example, the Stuxnet attack on Iran’s Natanz facility in 2010 demonstrated how malware exploited firmware vulnerabilities and SCADA system in order to physically destroy critical assets of the infrastructure [11–13, 37, 47]. Another example is the Ukraine blackouts of 2015 and 2016, caused by the BlackEnergy and Industroyer malware that exploited weak authentication mechanisms and weak protocols, which at the end led to power disruption on the national level [18, 21, 25]. In 2017, Triton/Trisis targeted Safety Instrumented Systems (SIS) in Saudi petrochemical plant and exploited insecure control mechanism. When it comes to Colonial Pipeline ransomware attack, weak VPN credential management vulnerability caused fuel shortage in East Coast. In Saudi Aramco, 30,000 hard disks were deleted due to compromised internal accounts and the abuse of access rights.
All of the described vulnerabilities that cyber threats exploited stress how important it is to understand the negative cause-and-effect relationship between vulnerabilities and cyber threats in the Smart Grid. If vulnerability exists, it will be exploited. Furthermore, in nearly all documented real-world cases, the detection of malware, ransomware, and other threats required several days, during which evident disruptions in energy distribution or internal system operations had already manifested [11, 13–15, 17, 18, 20, 25, 30, 31, 33, 55]. Most of the attackers stay under the radar in the system for a while in order to gather all necessary data for the attack to be fully successful and even more destructive.
4. Discussion
Table 3 highlights that insecure or weak protocols and poor communication are among the major issues and common vulnerabilities that facilitate cyberattacks in the Smart Grid. Insecure or weak protocols and poor communication are identified as significant weaknesses and potential vulnerabilities for cyber threats across nearly all types listed in Table 3. Certain types of cyber threats, such as firmware threats, insider threats, and phishing, do not rely directly on insecure or weak protocols. However, it is important to note that the most common threats mentioned in the literature (presented in Table 1), malware and DoS attacks, are primarily dependent on these insecure or weak protocols and communication methods. Other vulnerabilities mapped for malware and DoS attacks are weak authentication, inadequate access control, outdated systems, poor network design, and insecure Internet of things (IoT) devices. Alongside the most common vulnerability, weak, or insecure communication protocols, these factors create an optimal opportunity for cyber attackers to exploit Smart Grid systems. When addressing cyber threats, such as spoofing, Sybil attacks, and jamming, one of the most common vulnerabilities is the use of insecure or weak protocols and communication methods. Additionally, a significant vulnerability associated with these cyber threats is the lack of encryption or the use of ineffective encryption methods. Both the absence of encryption and poor encryption practices are particularly relevant to spoofing, Sybil attacks, and jamming. Cyber threats categorised as others, such as cross-site, blockchain, and sabotage, result from outdated software, human errors, or insufficient training. Additionally, there are risks associated with chip-level hardware vulnerabilities. APTs are linked to vulnerabilities, such as weak authentication, inadequate access control, legacy systems, outdated software, exposure of SCADA systems, and flaws in protocols. Insider threats and phishing arise from human error, insufficient training and awareness, a lack of standardised controls, and governance gaps. Vulnerabilities in firmware and devices lead to firmware threats. Conversely, data breaches, data falsification, unauthorised access and zero-day attacks arise from insecure or weak protocols, poor communication, lack of encryption or poor encryption, weak authentication, poor access control, firmware, and device vulnerabilities. Man-in-the-middle (MitM) attacks and ransomware stem from vulnerabilities such as insecure or weak protocols, poor communication, weak authentication, inadequate policies, strategic gaps, insufficient planning, human error, and a lack of training. Botnets originate from insecure or weak protocols as well as ineffective communication methods.
As mentioned previously, vulnerabilities and corresponding cyber threats do overlap. In order to reduce redundancy and get more clear view on the dependencies, Table 4 presents mapping of critical vulnerabilities and the corresponding cyber threats without overlapping. Both threats and vulnerabilities are grouped into five clusters (clusters were based on the similarities between categories, and grouping-related vulnerabilities under broader themes) and contain all the overlapping threats and vulnerabilities. Table 4 gives a more comprehensive and direct groups of the threats and vulnerabilities, whereas Table 3 gives a more fine-grained and in-depth overview of each threat and vulnerability present in the Smart Grid.
Table 4
Mapped critical vulnerabilities and the corresponding cyber threats without overlapping.
Names of the clusters in Table 4 describe the essence of vulnerability. For example, the first cluster named ‘authentication & access weaknesses’ consists of following vulnerabilities: weak authentication, poor access control, and insecure VPNs. Hence, the name of the first cluster: authentication and access weaknesses. It can be concluded from Table 3 that threats associated with authentication or access vulnerabilities are: malware, APTs, insider threats, unauthorised access, ransomware, and botnets. For the second cluster named ‘protocol and communication gaps’, which consists of insecure SCADA/ICS protocols (Modbus, DNP3, and IEC 60870), lack of encryption, and MitM vulnerabilities, the associated threats are: malware, DoS/DDoS, APTs, data falsification, and MitM injection. For the third cluster of vulnerabilities ‘legacy and device vulnerabilities’, the mapped threats are: malware, firmware exploitation, and cyber-physical sabotage. The fourth cluster is named ‘governance and policy gaps’, which contains lack of standardised controls, weak governance, and insufficient resilience planning vulnerabilities, which again correspond to APT entry vectors, phishing, and insider threats. The final cluster is named ‘human and organisational factors’, and it consists of human error, phishing susceptibility, and lack of training, which can be exploited by APT entry vectors, phishing, and insider threats.
Mapping of cyber threats and system vulnerabilities in the Smart Grid and energy infrastructure in general is highly useful in practice and can be applied in different fields. Table 5 gives a presentation of the areas where mapping of cyber threats and system vulnerabilities can be applied. The first column indicates application area; the second column describes and gives an example how mapping of threat and vulnerabilities can be applied, and the third column suggests the potential users. For example, mapping can be very useful for regulatory alignment. By prioritising threats and vulnerabilities, the findings provide a structured basis for demonstrating compliance with established cybersecurity regulations and standards, such as the European Union’s NIS2 (Directive on Security of Network and Information Systems 2) directive and the NERC CIP framework (North American Electric Reliability Corporation). This alignment is particularly relevant for policymakers and regulators, as it enables them to translate technical vulnerabilities into actionable regulatory requirements and oversight mechanisms. Furthermore, mapping of critical vulnerabilities and threats can be helpful in risk assessment frameworks, because it helps in enhancing risk assessment processes in the energy sector. Both energy providers and critical infrastructure operators can correctly enhance risk assessment processes. When it comes to defence strategy, mapping of cyber threats and system vulnerabilities can be crucial for developing efficient defence strategies (intrusion detection systems, network segmentation, or encryption). Finally, knowing the vulnerability that enables the threat can help in incident response by stressing correlation of vulnerabilities and specific attack vectors. Furthermore, the vulnerabilities that are identified in this paper can be mapped to a requirement of the NERC CIP standard. For example, weak authentication and poor access control can be mapped to CIP-005 (electronic security perimeter and access control), and legacy systems and outdated firmware can correspond to CIP-007 (system security management, patching, and updates). Weak incident reporting and response procedures can be correlated to CIP-008 (incident reporting and response planning).
Table 5
Practical application of threats and vulnerabilities mapping.
Furthermore, mapping of cyber threats and vulnerabilities can be used as a part of risk assessment frameworks in order to explain how human error, weak authentication, and insecure communication protocols continuously enable for cyberattacks to happen and be successful, while NIS2 focuses on systematic risk assessment, incident management, and employee awareness. The NERC CIP standards focus on who, and how, can access critical systems and on detection, response, and reporting of security incidents, which are directly reflected in unauthorised access via weak VPN credentials, legacy systems lacking updates, and unpatched firmware exploited in high-profile attacks like Stuxnet and Triton. This study can be viewed as an evidence-based mapping of the vulnerabilities that most often lead to the types of cyber threats and a suggestion on how high-level regulatory requirements with concrete and real-world attack pathways provide regulators, policymakers, and operators with a clearer foundation for prioritising compliance, strengthening defences, and directing resources with the most critical risks. Another application is in designing defence strategies. By understanding threat vulnerability mapping, a secure defence mechanism can be constructed in order to protect energy infrastructure. For example, the evident problem of insecure industrial protocols used in the energy infrastructure highlights the need for better encryption of industrial control protocols. Finally, threat vulnerability mapping can be useful for incident response and forensics. After a cyberattack, it is crucial to understand all steps undertaken by the attackers. Digital forensics is the best tool to uncover all the steps and potential entry points, attack process, and progression. Threat vulnerability mapping helps responders to focus their analysis and containment efforts more effectively.
There are several limitations to this study that have to be acknowledged. The study is based and relies on secondary literature reviewed in the systematic literature review, which again is a product of the lack of primary studies, research, and direct empirical evidence. Even though the study is based on secondary sources, its contribution lies in the first systematic mapping between threats and vulnerabilities in the energy sector and offers an insight that was not provided in the literature before. Another limitation is the fact that the literature analysed is predominantly in English, which may narrow down relevant studies that may explore correlations between threats and vulnerabilities within the energy sector. It is also important to stress that this study is specifically focused on the Smart Grid and energy infrastructure and cannot be fully applicable to all other types of critical infrastructure.
The future research should focus on developing real-time threat detection models, ideally utilising AI and machine learning. The goal of these models is to identify and respond to threats in real time within the Smart Grid. AI is increasingly integrated into IoT, especially within Smart Grids. This integration complicates the cyber threat landscape. Therefore, it is essential to continually improve and strengthen cybersecurity measures for Smart Grids. This paper does not focus on proposing specific solutions to address the vulnerabilities within the Smart Grid or on minimising associated threats. Instead, this research is dedicated to identifying correlations between cyber threats and vulnerabilities in the Smart Grid by mapping these threats to the identified vulnerabilities. For the future research, it would be beneficial to concentrate specifically on addressing these vulnerabilities and reducing the likelihood of cyberattacks that exploit them.
5. Conclusions
As critical structure is becoming even more endangered in the modern digital world, the need for deeper understanding of the cyber threats and the vulnerabilities of the energy infrastructure and system is becoming even more evident. Energy infrastructure as a part of critical infrastructure has been a target of cyberattacks numerous times in the last decade. There are many examples from the real-world cyberattacks on energy infrastructure that showed how multiple vulnerabilities of the system could be exploited by cyber threats. In order to be able to successfully defend the energy infrastructure, it is important to fully understand correlations between cyber threats and vulnerabilities of the system.
This paper conducted a systematic literature review in order to investigate whether particular vulnerabilities enable particular cyberattacks. As the research emphasises, weak protocols and poor communication are primary weaknesses of the Smart Grid. Insecure or weak protocols and inadequate communication are major cyber threat vulnerabilities across nearly all types of cyber threats. Firmware, insider threats, and phishing threats do not directly use insecure protocols [6, 43, 51, 52]. Malware and DoS attacks are the most common threats in the literature and they rely on these vulnerable protocols and communication mechanisms [7, 8, 35–39]. Malware and DoS attacks also target weak authentication, access control, old systems, poor network design, and vulnerable IoT devices [7, 8, 35–39]. These elements, along with the most typical vulnerability, weak or unsecure communication protocols, make Smart Grid systems ideal for cyberattacks. Insecure protocols and communication methods are a typical vulnerability for cyber threats, such as spoofing, Sybil attacks, and jamming [6, 43, 51, 52]. These cyber risks are also vulnerable to lack of or poor encryption [6, 8, 37, 48, 50, 59, 68]. Lack of encryption and bad encryption methods affect spoofing, Sybil attacks, and jamming [45, 47, 65, 67]. Other cyber threats include cross-site, blockchain, and sabotage originating from old software, human errors, or inadequate training [44, 48–50]. Additionally, chip-level hardware vulnerabilities pose danger. APTs are linked to weak authentication, access control, legacy systems, outdated software, SCADA system exposure, and protocol issues. Human mistakes, poor training and poor awareness, unstandardised processes, and governance gaps cause insider threats and phishing. Device and firmware vulnerabilities cause firmware threats [6, 43, 51, 52]. Insecure protocols, inadequate communication, lack of encryption, weak authentication, poor access control, firmware, and device vulnerabilities cause data breaches, data fabrication, unauthorised access, and zero-day attacks [8, 35, 38, 46]. MitM attacks and ransomware are caused by insecure protocols, poor communication, weak authentication, inadequate policies, strategic gaps, insufficient planning, human mistake, and lack of training [41, 54, 59]. Insecure protocols and communication mechanisms cause botnets.
It is vital to point out that some of the weaknesses are the same for different kinds of cyber threats. This is because, in real life, different forms of energy infrastructure and system vulnerabilities depend on one another, which means that vulnerabilities cannot be completely separated from one another. Malware, APTs, ransomware, and botnets exploit weak authentication and insecure protocols. Legacy systems and bad segmentation, on the other hand, are to blame for both cyber-physical sabotage and data breaches. Mapping the vulnerabilities and cyber threats in Smart Grid and energy infrastructure shows that a small number of important vulnerabilities can lead to many cyber threats. This shows again, why we need integrated and systemic defence methods. The Stuxnet attack on Iran’s Natanz facility in 2010, for instance, showed how malware might use firmware and SCADA system weaknesses to physically damage important parts of the infrastructure [11–13, 37, 47]. The 2015 and 2016 blackouts in Ukraine and the BlackEnergy and Industroyer viruses that took advantage of weak authentication and protocols are further examples. These events caused power outages on a national level [18, 21, 25]. In 2017, Triton/Trisis attacked safety instrumented systems (SIS) at a petrochemical plant in Saudi Arabia and took advantage of a weak control mechanism. The Colonial Pipeline ransomware attack caused a fuel scarcity on the East Coast because of a flaw in how weak VPN credentials were handled. Saudi Aramco erased 30,000 hard drives because of hacked internal accounts and the misuse of access permissions. All of the weaknesses that cyber threats took advantage of show how vital it is to understand the negative cause-and-effect link between vulnerabilities that cyber threats in the Smart Grid. If the weakness is there, it will be used against the system.
The findings of this paper align closely with the requirements of the NIS2 Directive as well as NERC CIP standards, such as CIP-005 on access control, CIP-007 on patch management, and CIP-008 on incident reporting. The practical implications of the findings extend to multiple domains: regulatory alignment, risk assessment frameworks, improvement of defence strategy, and incident response and forensics.